
Some of the most famous computer data breaches ever reported bypassed perimeter cybersecurity defenses. Instead of finding weaknesses in software, the hackers relied on weaknesses in human beings.
For example, Hillary Clinton’s 2016 campaign manager’s email was compromised by a phishing email pretending to be from Gmail. In 2008, hackers broke into a Department of Defense network not linked to the internet because employees purchased infected USB flash drives at a Kabul kiosk and inserted them into network laptops.
Expensive and sophisticated cybersecurity systems can only do so much. They can’t do anything to help when an employee falls for a phishing email, leaves a password on a sticky note, or plugs infected hardware into a secure network.
Hackers are opportunistic parasites who will always look for the weakest link into businesses and organizations. Employees are often the weakest link. Verizon’s 2019 Data Breach Investigations Report found that nearly one-third of data breaches the year before involved phishing.
The good news is that employee training can thwart hacking attacks that target employees. And basic employee training is relatively inexpensive. This eBook highlights the best practices that can keep employees from falling to both the latest phishing scams and well as the overlooked dangers of good old fashioned non-tech related espionage.

Not a problem! Enter your email below for a downloadable PDF version that you can get to on your own time.
Some high tech crime can be thwarted by following some low-tech best practices. It all starts at employee workstations, which can hold a treasure trove of loot for people who want to steal your organization’s secrets.
It makes complete sense and sounds so simple, but keeping a clean desk is often overlooked when talking about data security. It’s also the perfect place to start the discussion with employees.
Employees that keep a cluttered desk tend to leave USB drives and smartphones out in the open. They also often forget to physically secure their laptops so someone can’t simply walk off with them.
A messy desk also makes it more difficult to realize something is missing such as a folder with hard copy print-outs of customer lists. In addition to increasing the likelihood of something being removed, a cluttered desk means that the discovery of any theft will likely be delayed— perhaps by days or even weeks if the employee is out of the office. Such delays make it more difficult to determine who the perpetrator is and where the stolen material might have been taken.
Encouraging employees to maintain a neat desk pays off in two ways. In addition to making digital and paper assets more secure, employees with clean desks are more apt to be productive because they can quickly—and safely—access the tools and resources they need to do their jobs.
Phishing is defined as a fraudulent attempt to obtain sensitive information by disguising oneself as a trustworthy entity. In order to trick people, hackers impersonate a wide variety of people and institutions, including coworkers, IT staff, email system administrators, banks, the IRS and police.
In especially dangerous “spear phishing” attacks, the scam can be personally directed. The hacker uses information about their target to increase the apparent credibility of their request for more sensitive information.
The scope of phishing attacks is constantly expanding, but frequent attackers often utilize one of these four tactics:
Just as keeping a clean desk makes it harder for thieves to walk away with documents, following best practices for email cybersecurity can lessen the risk of falling victim to phishing attacks.
Employees should always be suspicious of potential phishing attacks, especially if they don’t know the sender. Here are five best practices to follow.
It’s better to learn to fight phishing attacks in a controlled environment than when actual data is on the line, which is why many employers today conduct phishing tests on their own employees. Think of them as training exercises similar to fire drills and active shooter scenarios.
To conduct a phishing test, follow these guidelines:
If your employees are using passwords like “password,” the name of your organization, or “qwerty,” it’s about as useful as having no password at all.
Hackers are sure to try lists of most common passwords when trying to gain access, and these passwords are easy to guess or look up.
The following common passwords were collected from Troy Hunt’s database of global cyber breaches, as reported by Forbes.
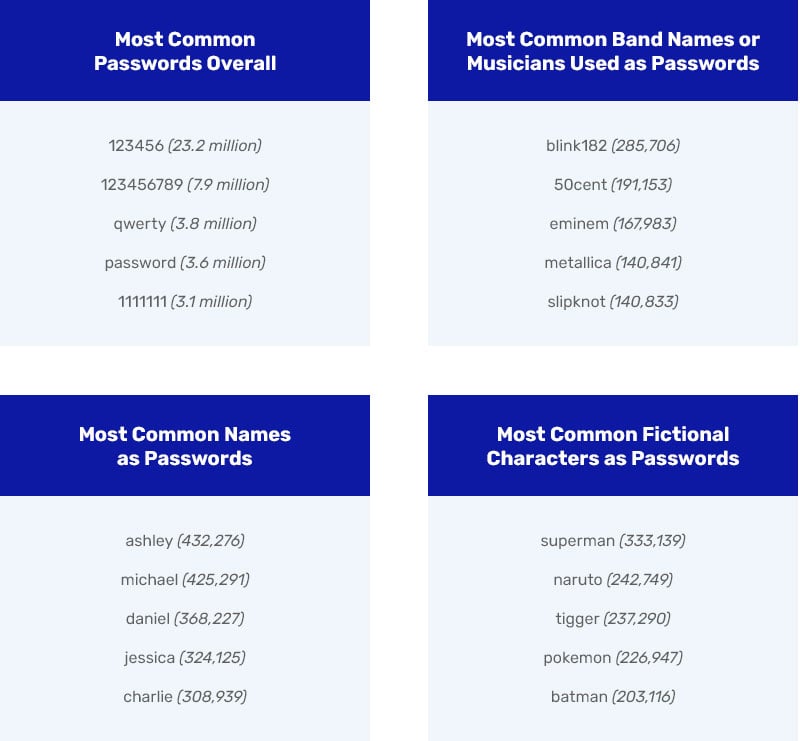
It’s easy to avoid the weakest passwords, but it’s hard to consistently come up and remember good passwords. Passwords should ideally be strong (a long un-guessable string of letters, numbers, and symbols). They should also be unique: not used as the passwords for other websites. Keeping track of a long list of strong, unique passwords is a formidable task, which is why using a password manager is a top tip for strengthening password security. A password manager also saves the time and stress that usually goes into creating and remembering multiple passwords. A password manager can make rebounding from a breach easier with a single reset of multiple passwords with their strong password generators.
While securing usernames isn’t as important as keeping passwords private, usernames are one of the pieces of information hackers need to get access, so it’s worthwhile to avoid commonly guessed account names like “admin” and “user1.”
The prevalence of large data breaches means that millions of passwords are out in public or are available for sale on the dark web. When people repeat passwords, they let hackers who already have a key to one account access all the other accounts that share the password.
While it may be a helpful memory trick, using simple variations of passwords, like changing “OpenSeasame” in one account to “Open3easame” isn’t a safe alternative to using unique passwords for every account. It’s too easy for hackers to try out different variations of a password once they have a related one.
Have your employees check their email address on haveibeenpwned.com to see which of their accounts are already compromised by existing data breaches. They should prioritize changing their passwords on compromised sites and any sites that share a password with the breached site.
Like it or not, private employee mobile devices in the workplace are a given today. For years, corporate IT departments resisted the idea of bring your own device (BYOD) policies specifically because of the security risks that come with putting sensitive proprietary information onto devices that the organization doesn’t own.
But BYOD appears to be the way of the future because it’s just an easier and less expensive way for companies to keep pace with the constant innovations in the consumer electronics market. Plus, employees report they’re more productive using their own phones, laptops and tablets compared to using company-issued ones.
Protecting important data in a BYOD world means being aware of security challenges that come from employee-owned devices, and educating your employees.
Because employee phones are effectively part of a business’s network once they connected, employers today share responsibility for keeping their employees’ devices secure.
A Mobile Device Management platform is a kind of middle ground between a company phone and a purely private BYOP phone. An MDM platform is a software that lets businesses’ manage aspects of employee devices.
MDM features include the ability to:
Some of the most devious attempts to steal information, identities, and access to devices occur within the internet browser window.
Employees can best defend themselves by familiarizing themselves with the most common techniques. Two especially common browser-based techniques are malvertising and social media scams.
Keeping browsers and operating systems up-to-date can also help minimize vulnerabilities.
Today’s BYOP world puts a heavy weight on employees and on IT departments.
But they don’t have to be alone. Managed service providers (which include us at Meridian Imaging Solutions) can help supplement the work of IT departments.
Security services that MSPs can provide include:
Any managed service provider should provide protection against malware and viruses.
It’s worth taking a moment to understand the difference between malware and viruses, because there’s so much confusion in this area.
Technically, viruses are a type of malicious code that’s capable of replicating itself to do damage to computers of data. Meanwhile, malware is an umbrella term that applies to all malicious code, including viruses.
But there’s a distinction when it comes to protection programs. Antivirus software traditionally focuses on legacy malware like Trojans, viruses and worms, all of which continue to be threats. Anti-malware software, meanwhile, focuses on new and emerging threats. That’s why we recommend both anti-malware and antivirus protection. We provide - and recommend - malware protection through Malwarebytes, and virus protection from Webroot.
There’s a common but misguided attitude in many organizations that cybersecurity is the job of the professions in the IT department and that others don’t need to worry about it. This attitude is often found in back office departments like accounting and legal departments. It’s a dangerous attitude because these employees often have access to sensitive information, and their reluctance to learn about cybersecurity threats make them especially vulnerable.
There’s an equally dangerous attitude that’s common among more tech savvy employees: that “low-tech” social engineering attacks like phishing only work on gullible people who don’t understand technology. This attitude is equally dangerous because it underestimates the sophistication of these attacks and how easy it is to fall for a well-crafted message that appears to come from a trusted person.
The guidelines suggested in this book will likely change as hackers develop new tactics. But one guideline that won’t change in the foreseeable future is that cybersecurity is everyone’s job today.
Your network assessment will give you insight into the true status of your IT system, and point the way to appropriate corrective actions you can make to secure your business effectively and efficiently.


888-289-2776
info@whymeridian.com
Meridian Imaging Solutions
1595 Spring Hill Rd, Suite 450
Vienna, VA 22182
© 2025 Meridian Imaging Solutions | Privacy Policy